Windows Risk Eliminator is a malicious program that uses a number of misleading techniques to make a hefty profit out of unsuspecting victims. This program is classified as a rogue security tool because it pretends to scan your computer for malware and reports system threats which do not even exist. Cyber-criminals spread their malware through the use of Trojan Downloader and fake online scanners. Victims are typically tricked into paying for additional tools or services. This rogue costs almost $80 with a lifetime support. You can get perfectly legitimate anti-malware software for about $40. Windows Risk Eliminator gives a false sense of security. It displays fake security alerts and notifications saying that your computer is infected with some sort of malware. Furthermore, Windows Risk Eliminator claims that you can make your computer run faster if you pay for a additional tools that will fix numerous system/registry errors. Please do not fall victim to this scam and remove Windows Risk Eliminator from your computer as soon as possible. What is more, this scareware blocks other programs on the victims computer. It blocks web browsers, task manager, registry editor and of course anti-malware software. Thankfully, weve got the step-by-step removal instructions to help you to remove Windows Risk Eliminator malware. Last, but not least, if you have purchased this bogus program, please contact your credit card company and dispute the charges. If you need help removing Windows Risk Eliminator, please leave comment. You can post additional information about this rogue too. Good luck and be safe online!
Windows Risk Eliminator is from the same family as
Windows Universal Tool,
Windows Utility Tool, and
Windows Security & Control.
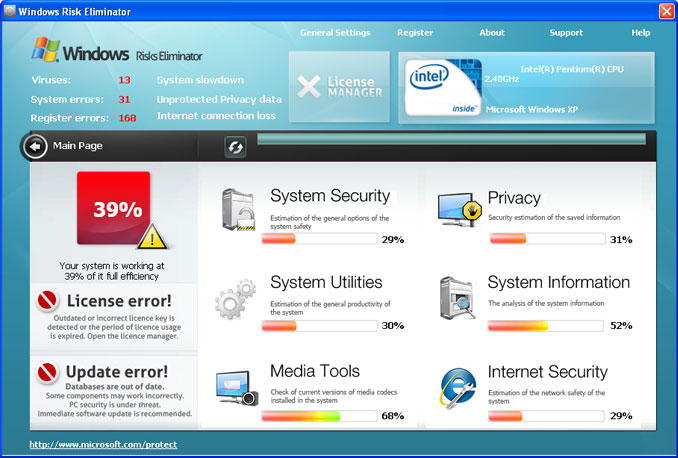
Fake Windows Risk Eliminator scan results:
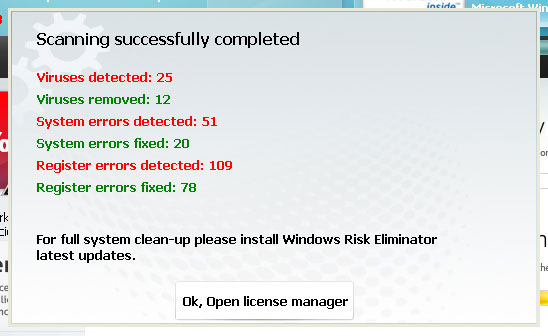
Fake security alert saying that taskmgr.exe is a key-logger:
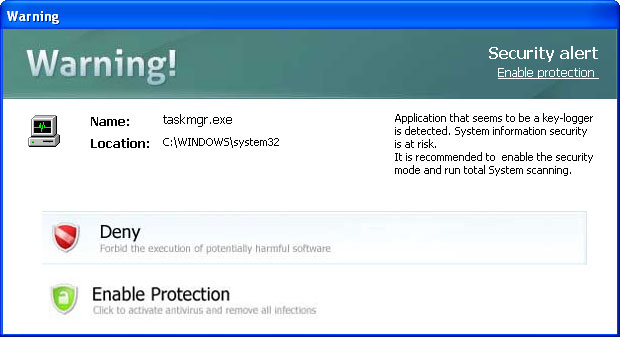
A web form where you can purchase Windows Risk Eliminator:
Windows Risk Eliminator removal instructions:1. Rename the main executable of Windows Risk Eliminator:
In Windows XP:
C:Documents and Settings[UserName]Application Data[SET OF RANDOM CHARACTERS].exe
In Windows Vista/7:
C:Users[UserName]AppDataRoaming[SET OF RANDOM CHARACTERS].exe
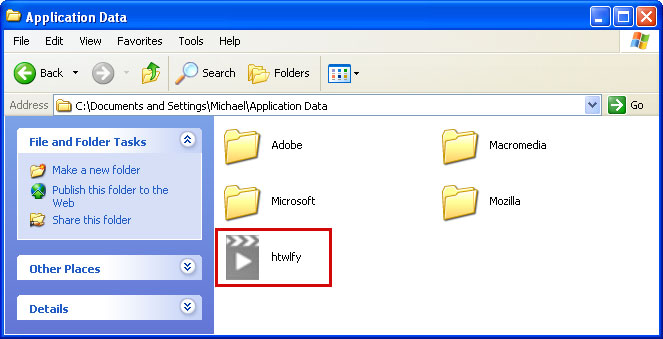
Look for
htwlfy or similar file and rename it to
malware. Then restart your computer. This should disable Windows Risk Eliminator. After reboot, please continue with the rest of the removal process. NOTE: By default, Application Data folder is hidden. If you can find it, please read
Show Hidden Files and Folders in Windows.
OR you can download
Process Explorer and end Windows Risk Eliminator process.
2. Download
shell-fix.reg. Double-click to run it. Click "Yes" when it asks if you want to add the information to the registry. This file will fix the Windows Shell entry.
3. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to
iexplore.exe or
winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Dont forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32 Antivirus.
Alternate Windows Risk Eliminator removal instructions (in Safe Mode with Networking):1. Reboot your computer is "
Safe Mode with Networking". As the computer is booting tap the "
F8 key" continuously which should bring up the "
Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here:
http://www.computerhope.com/issues/chsafe.htm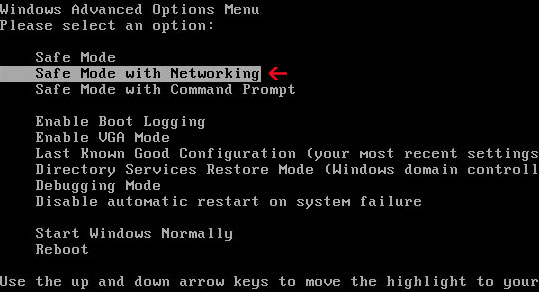
NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to
iexplore.exe or
winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Dont forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32 Antivirus.
Associated Windows Risk Eliminator files and registry values:Files:
In Windows XP:
- C:Documents and Settings[UserName]Application Data[SET OF RANDOM CHARACTERS].exe
In Windows Vista/7:
- C:Users[UserName]AppDataRoaming[SET OF RANDOM CHARACTERS].exe
Registry values:
- HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionWinlogon "Shell" = "%UserProfile%Application Data[SET OF RANDOM CHARACTERS]"
Share this information with other people:































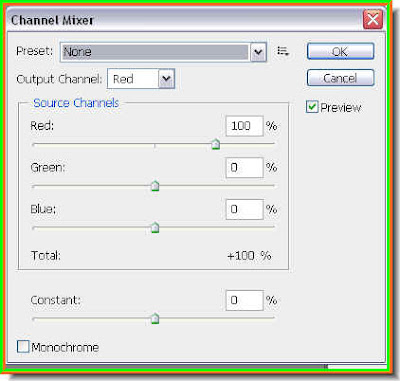


 Step 11 : Since we are using Adjustment Layers, the Channel Mixer is on a separate layer above the layer with the photo of the girl, which is Layer 1.
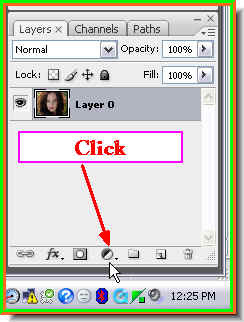
Step 11 : Since we are using Adjustment Layers, the Channel Mixer is on a separate layer above the layer with the photo of the girl, which is Layer 1. Step 12 : Click the New Fill and Adjustment Layer button again.
Step 12 : Click the New Fill and Adjustment Layer button again.
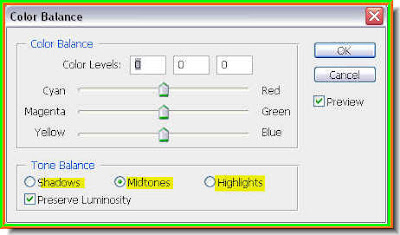



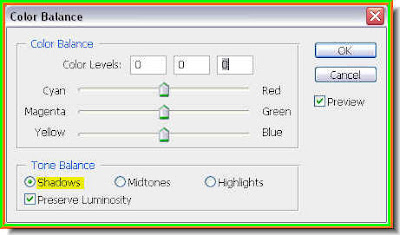


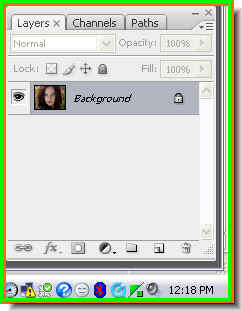
 Lastly, this how you Layers pallette looks. The Color Balance layer is on top as we used it the last. It is above the Channel Mixer layer, which above the photo of the girl in Layer 1. Since these are adjustment layers, the actual photo has not been affected. If ytou click off the eye icon on the Color Blance and Channel Mixer layers, you will be able to see the original photo.
Lastly, this how you Layers pallette looks. The Color Balance layer is on top as we used it the last. It is above the Channel Mixer layer, which above the photo of the girl in Layer 1. Since these are adjustment layers, the actual photo has not been affected. If ytou click off the eye icon on the Color Blance and Channel Mixer layers, you will be able to see the original photo.
